Linux, a popular operating system known for its flexibility and power, relies on a robust permissions system to manage access to files and directories. However, for beginners, understanding Linux permissions can be daunting and confusing. In this article, we'll take a deep dive into Linux permissions and demystify the concept, providing a comprehensive guide for new users. We'll cover the basics, including permission types, permission syntax, and how to interpret permission output. We'll also explore practical examples and best practices to help you gain confidence in managing Linux permissions.
Understanding Linux Permissions
Linux permissions govern how users and groups can interact with files and directories. There are three types of permissions: read (r), write (w), and execute (x). Here's an overview:
Read (r): Allows users to view the contents of a file or the names of files in a directory.
Write (w): Allows users to modify the contents of a file or create, rename, or delete files in a directory.
Execute (x): Allows users to execute a file as a program or traverse a directory.
Permissions are assigned to three different entities: the owner, the group, and others. The owner is the user who created the file or directory, the group is a collection of users with similar permissions, and others refer to everyone else.
Permission Syntax Linux permissions are represented using a combination of letters and symbols. The basic syntax for permissions is as follows:
rwxrwxrwx
Each set of three characters (rwx) represents the permissions for the owner, group, and others, respectively. The letters can be replaced with hyphens (-) to indicate the absence of a particular permission.
For example:
rwxindicates that the user has read, write, and execute permissions.r-xindicates that the user has read and execute permissions, but not write permissions.r--indicates that the user has only read permissions.
Interpreting Permission Output When you use the ls -l command to list files in a directory, you'll see a long listing that includes the permissions for each file or directory. Here's an example:
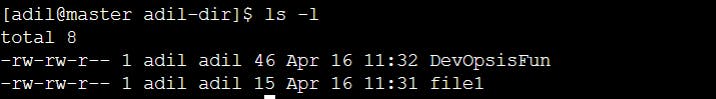
Let's break it down:
The first character represents the file type: "-" for a regular file, "d" for the directory, "l" for a symbolic link, and so on.
The next nine characters represent the permissions for the owner, group, and others, respectively.
The number "1" indicates the number of hard links to the file.
The first "adil" and second "adil" represent the owner and group of the file, respectively.
The number "46" represents the file size in bytes.
"Apr 16 11:32" indicates the date and time of the last modification.
"DevOpisFun" is the name of the file.
Practical Examples of Managing Linux Permissions
Let's explore some practical examples of managing Linux permissions to understand how they work in real-world scenarios.
Modifying Permissions with chmod
The chmod command is used to change the permissions of files and directories in Linux. Here's an example:
chmod u+x file1
This command adds execute permission to the owner of the file "file1". You can also use "g" for the group and "o" for others, and combine permissions using "+", "-", or "=" to add, remove, or set permissions, respectively.
Changing Ownership with chown
The chown command is used to change the owner and group of files and directories. Here is an example:
chown newuser:newgroup file.txt
This command changes the owner of the file "file.txt" to "newuser" and the group to "newgroup". You can also use the "-R" option to recursively change ownership for all files and directories within a directory.
Understanding Special Permissions
In addition to the basic read, write, and execute permissions, Linux also has some special permissions that provide additional functionality.
These are:
Setuid (s): When set on an executable file, it allows the user who executes the file to temporarily gain the privileges of the owner. For example, if a file has the setuid permission set for the owner, when any user executes that file, they will temporarily have the same privileges as the owner of the file. This can be useful in certain cases where a user needs to perform actions that require higher privileges, such as changing passwords or performing system-level tasks. For example,
chmod u+s fdisksets the setuid permission for the owner.Before setuid
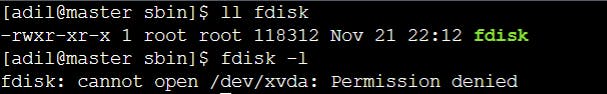
After setuid

Setgid (s): When set on a directory, it allows files created within that directory to inherit the group ownership of the parent directory. For example, if a directory has the setgid permission set for the group, any new file created within that directory will automatically have the same group ownership as the parent directory. This can be helpful in scenarios where multiple users need to collaborate and share files within a common group. For example,
chmod g+s directorysets the setgid permission for the group.Sticky bit (t): When set on a directory, it restricts deletion of files within that directory to only the owner of the file, the directory's owner, or the superuser. This means that even if other users have write permissions on the directory, they won't be able to delete files that they don't own. The sticky bit is often used on directories that are publicly accessible, such as temporary directories, to prevent the accidental deletion of files by other users. For example,
chmod +t directorysets the sticky bit permission.Best Practices for Managing Linux Permissions
Here are some best practices to keep in mind when managing Linux permissions:
Avoid using excessive permissions: Grant permissions only as necessary to minimize security risks.
Regularly review and update permissions: Keep track of permissions and update them as needed to ensure proper access control.
Use symbolic links with caution: Permissions of the target file are applied to the symbolic link, so be mindful of potential security implications.
Be cautious with setuid/setgid permissions: Use them judiciously, as they can potentially elevate privileges and pose security risks.
Keep backups of important files: Mistakes in permission changes can happen, so always have backups of important files to restore them if needed.
Conclusion
Mastering Linux permissions is a crucial skill for new Linux users, and it's essential for managing file access and maintaining security. By understanding the basics of permission types, syntax, and interpreting permission output, as well as learning practical examples and best practices, beginners can gain confidence in navigating the Linux permissions system. Remember to always prioritize security and follow best practices to ensure proper access control and protect your system. With practice and experience, you'll become proficient in managing Linux permissions and effectively controlling access to your files and directories.
So, there you have it! We hope this comprehensive guide on demystifying Linux permissions has provided you with a clear understanding of this important aspect of Linux file system management. With this knowledge, you can confidently navigate and manage permissions for your files and directories in Linux, ensuring secure and efficient system operation. Happy exploring and experimenting with Linux permissions!

